2025 Phishing Simulation
If you were redirected to this page, you fell for our phishing simulation. Don't worry, this was just a test - no passwords were captured, and your ShareFile account is not in danger
This phishing simulation was designed to emulate an attack where a hacker sends out targeted phishing emails to SEM employees and our advisors.
Phishing attacks continue to be extremely widespread and one of the most effective ways for a hacker to gain access to you and your company. SEM conducts periodic phishing simulations to make sure that we and our business partners are aware of the techniques used by cyber criminals. When it comes to security, your success is our success and vice versa.
Let's review some “red flags” in this simulated attack:
Email:
This is the phishing email you received:
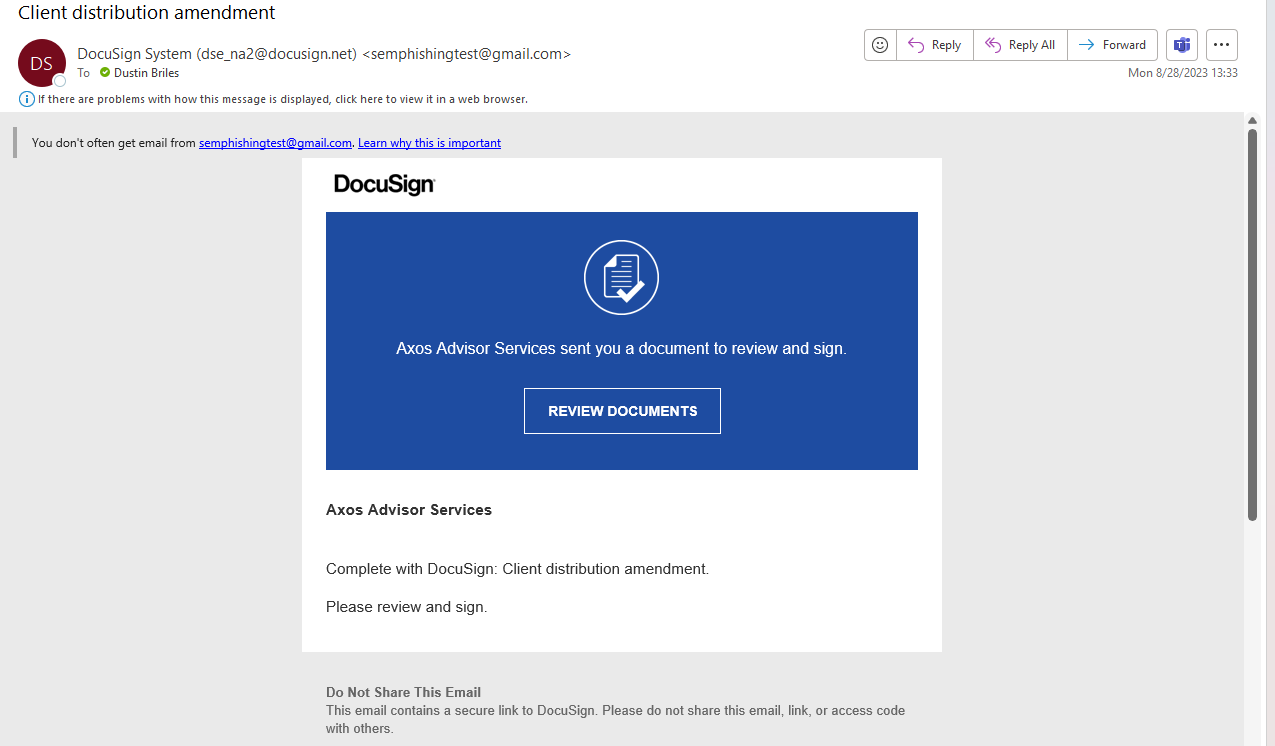
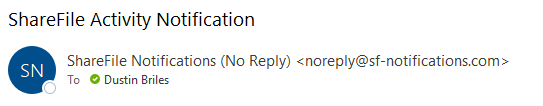
Email Address
Legitimate ShareFile upload/download notification emails only come from [email protected].
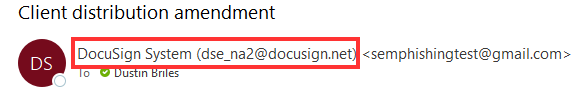
When you send an email, it will often contain a Display Name. Most of the time, your email client will set your display name for you - often it'll be your name, e.g. “John Smith”. However, with a little technical knowledge, you can set the Display Name to whatever you want.
This phishing email set the display name to ShareFile Notifications (No Reply), which is exactly what the display name in a legitimate ShareFile notification email is - but the phishing email did not come from ShareFile.
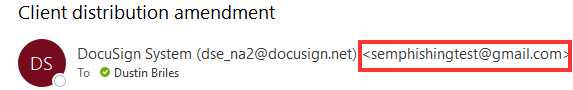
There is more information to the right of the Display Name. The actual email address here is: semwealth-sharefile.com
Notice the display name and email address in a legitimate email from ShareFile - the display name is the same as the phishing email, but the real email address it came from is [email protected]
Email Content
Spotting "red flags" in the email requires you to think critically about the content and context of the email. Here are some examples:
- "You don't often get email from..." - Your email provider may have the ability to configure a banner which warns you when you receive email from an uncommon / new sender. If you haven't configured this, we strongly recommend that you do. Notice the banner shows the real from address. In Microsoft 365, this feature is called First contact safety tip
- Generic content / vague details - compare the phishing email to a legitimate ShareFile notification email. You should notice the name of the file that was "uploaded" (and the path it was uploaded to) in the phishing email are a lot less specific than in legitimate ShareFile notification emails. We normally include specific client or account information in the names of uploaded files so that they can be easily identified
- Unexpected - you should also consider if the email you received was something that you expected to receive. For example, in this case, you probably would not hear about a custodian changing their fees for the first time through a file uploaded to ShareFile. Unexpected communication can be a red flag.
Individually, the "red flags" in the email don't guarantee that this it is a phishing email. Some legitimate emails do want to convey a sense of urgency, or have vague details, etc. Each individual "red flag" is cause for concern and should increase your level of scepticism, but you should consider things wholisticly. The more red flags, the more likely it is that the email is not legitimate.
Some other tips:
- If possible, go directly to the website using a known good link (like a Bookmark), even if you're pretty sure that the link is legitimate. This is not possible with certain kinds of emails (e.g. password resets)
- If you're unsure, you can ask someone else to look at the email and/or try to contact the sender to ask if the email is legitimate.
- If you do contact the sender, don't reply directly to the phishy email. If possible, don't send them an email at all. If an attacker has control of the mailbox you're replying to, they can simply reply to your email and say "yes this is legitimate". Use a different form of communication, like a phone call.
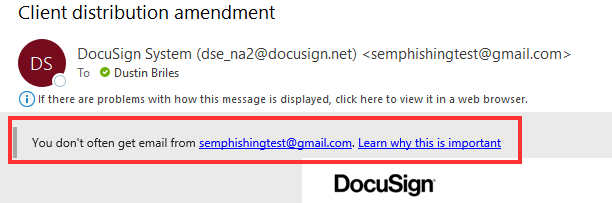
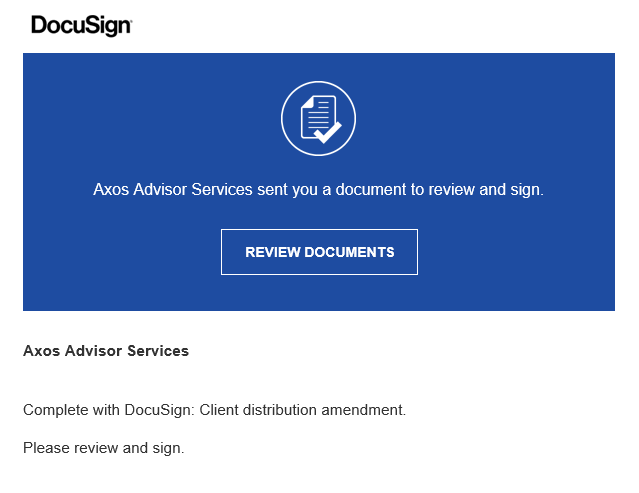
Link URL
In general, you should avoid clicking links in emails if at all possible. You can inspect the link, but sometimes even legitimate links look a little scary or are hard to make sense of. A better plan is to go directly to the website and look for the information you need.
There are some situations - like a password reset email - where you may have to click the link. In these situations, you will want to take the other factors (email address, context, email content) into serious consideration before clicking - inspecting the link doesn't always make things clearer.
All that said, inspecting the link URL is still an (imperfect) tool in our toolbelt:
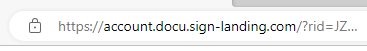
If you preview the link URL (hover over it on a computer, long-press it on a mobile device) in the phishing email, you will notice the domain is semwealth-sharefile.com. This is a lookalike domain - it is designed to look like a legitimate ShareFile domain, but it is not. The actual domain for SEM's ShareFile website is semwealth.sharefile.com - notice the period instead of the hyphen. We registered that lookalike domain to host the phishing site, which is absolutely something a real phishing attack would do.
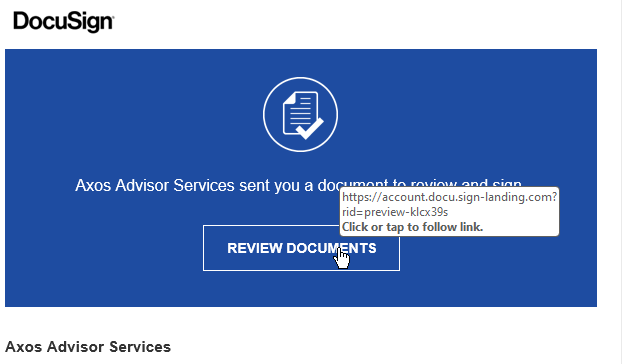

Landing Page
It is possible you could be compromised even if you just click the link in a phishing email. However, it is still advantageous to know how to identify a phishing web page because the goal of many phishing attacks is to get you to input your login credentials on a fake web page. Let's look at some "red flags" on this phishing web page:
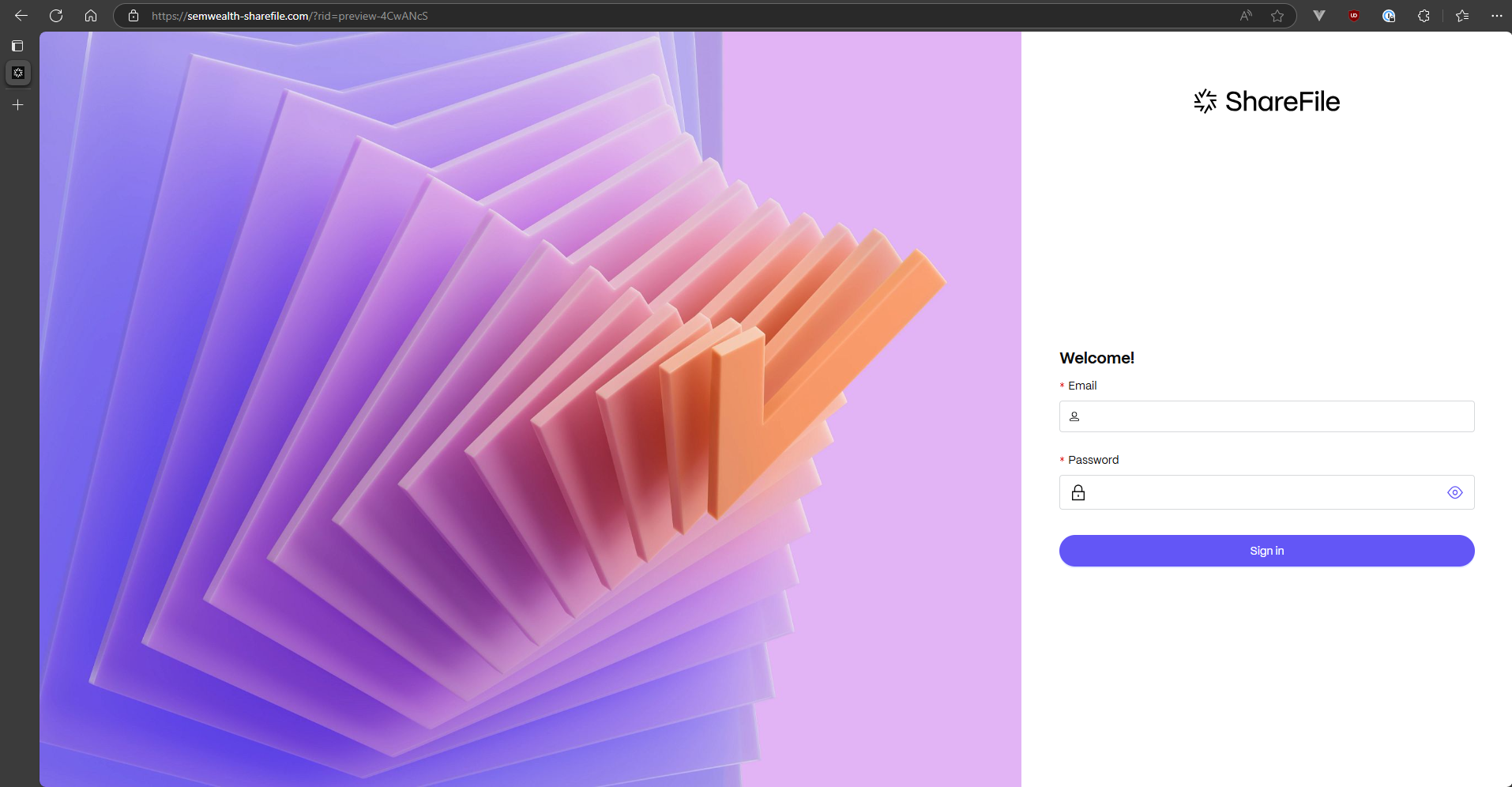
Password manager
If you have a password manager, you should have noticed that it did not autofill or have any suggestions for you on this page. If your password manager does not suggest login credentials on a web page where it normally does, this is a big red flag - this is a huge red flag that you're not on a legitimate webpage.
If you don't have a password manager, this is one of many reasons that they are a good idea!
Unfortunately, even this isn't a perfect indicator - sometimes applications will change the URL of their login page, which means your password manager won't suggest passwords on a totally legitimate webpage. If this happens, you can update/add the new URL in your password manager and it will suggest credentials in the future (just make sure the webpage at the new URL is actually legitimate first!)
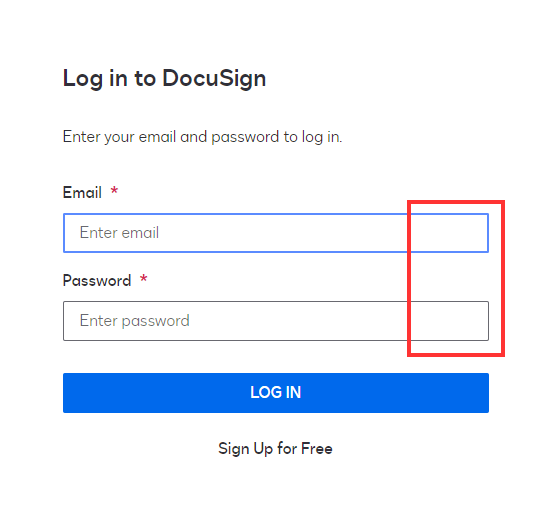
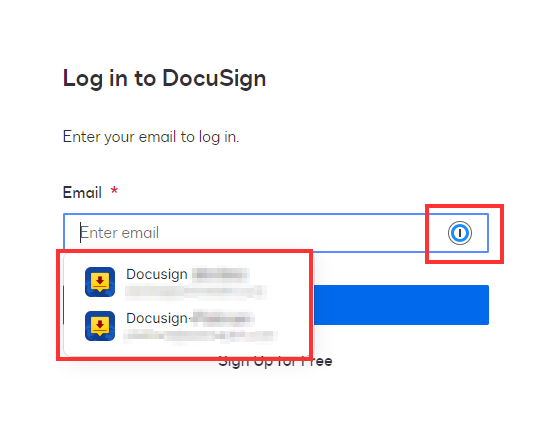
URL
If you're reading this and don't have a password manager, stop what you're doing and go get one! Password managers have many benefits and are, in general, much better at deciphering URLs than the average human. However, it can still be useful to know what to look for yourself.
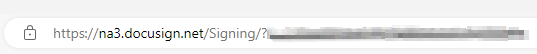
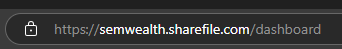
Look closely at the URL. Everything between https:// and the next / is the domain name. In this case, it is semwealth-sharefile.com. This is the same lookalike domain we saw in the link in the phishing email. The domain for a legitimate ShareFile website is either auth.sharefile.io (for the login page) or [company name].sharefile.com (after you log in), where [company name] is the specific subdomain of the ShareFile tenant you're logging in to.
You might have noticed the padlock icon to the left of the URL. This does not mean that the website is safe! It just means that the connection to the website is encrypted. For more information: What does the padlock in your address bar really mean?
Further Reading
Troy Hunt, a prominent figure in the world of cybersecurity, fell victim to a phishing attack earlier this year. This goes to show that even the professionals must stay vigilant! Check out his blog post detailing what happened: https://www.troyhunt.com/a-sneaky-phish-just-grabbed-my-mailchimp-mailing-list/
Questions?
If you have any questions about the content on this page, or our phishing simulations in general, feel free to email us at [email protected]
